Master the Art of Cyber Security Hacking: Your Comprehensive Step-by-Step Guide to Becoming a Cyber Security Expert

In today's increasingly digital world, the demand for cyber security professionals is at an all-time high. With threats to data and systems constantly evolving, organizations are desperately seeking individuals who possess the knowledge and skills to protect their assets. If you're interested in a career in cyber security hacking, or simply want to enhance your understanding of this fascinating field, then this comprehensive guide is your ultimate resource.
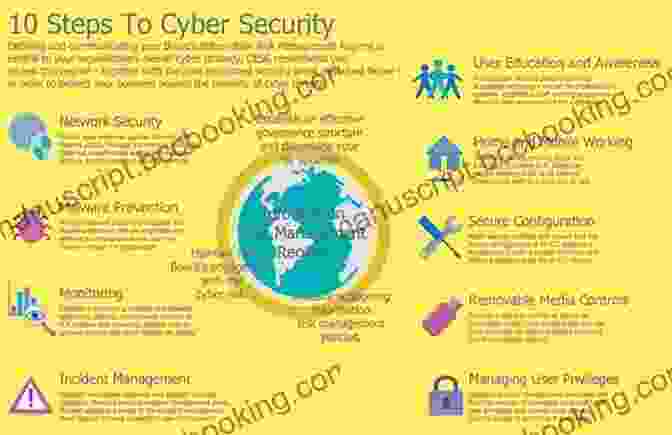
Chapter 1: The Basics of Cyber Security
Before delving into the technicalities of hacking, it's essential to establish a solid foundation. This chapter will introduce you to the fundamentals of cyber security, including:
4.3 out of 5
| Language | : | English |
| File size | : | 2559 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 177 pages |
| Lending | : | Enabled |
- Common cyber threats and attacks
- Cyber security architecture and principles
- Ethical hacking and the importance of responsibility
Chapter 2: Understanding Network Security
Networks are the backbone of any digital infrastructure. In this chapter, you will gain an in-depth understanding of network security, covering:
- Types of network attacks and vulnerabilities
- Firewalls, intrusion detection systems, and other protective measures
- Network monitoring and incident response
Chapter 3: Diving into Operating System Security
Operating systems control the core functionality of computers. This chapter will explore operating system security, focusing on:
- Common vulnerabilities and exploits targeting operating systems
- Hardening and securing operating systems
- Virtualization and its impact on security
Chapter 4: Web Application Security
Web applications are ubiquitous in today's digital landscape. This chapter will guide you through the intricacies of web application security, covering:
- Web application vulnerabilities such as SQL injection and cross-site scripting
- Secure coding practices and testing methodologies
- Best practices for protecting web applications from attacks
Chapter 5: Cryptography and Data Protection
Cryptography plays a vital role in safeguarding sensitive data. This chapter will introduce you to:
- Encryption algorithms and key management
- Data protection technologies like hashing and digital signatures
- Case studies of cryptographic attacks and their prevention
Chapter 6: Social Engineering and Physical Security
Cyber security is not just about technology. This chapter will emphasize the importance of social engineering and physical security, covering:
- Social engineering techniques used by attackers
- Physical security measures to protect against unauthorized access
- Employee training and awareness
Chapter 7: Penetration Testing and Ethical Hacking
Penetration testing is a crucial aspect of cyber security. This chapter will walk you through:
- Types of penetration tests and their methodologies
- Tools and techniques used in ethical hacking
- The importance of vulnerability assessment and reporting
Chapter 8: Cyber Security Incident Response and Forensics
In the event of a cyber security breach, incident response is essential. This chapter will cover:
- Incident handling procedures and best practices
- Forensic investigation techniques
- Case studies of major cyber security incidents
Chapter 9: Cyber Security Compliance and Regulations
Organizations face a complex landscape of cyber security compliance and regulations. This chapter will discuss:
- Major cyber security regulations and their requirements
- Compliance frameworks and best practices
- The role of cyber security in risk management
Chapter 10: The Future of Cyber Security
Cyber security is a constantly evolving field. This chapter will provide insights into:
- Emerging trends and technologies in cyber security
- The impact of artificial intelligence and machine learning on cyber security
- Career opportunities and professional development in cyber security
This comprehensive guide provides you with the knowledge and skills you need to embark on a successful career in cyber security hacking. Whether you're a complete beginner or an experienced professional, this book will empower you to protect yourself and your organization from the evolving threats of the digital world.
Free Download your copy today and become a master of the cyber security hacking!
4.3 out of 5
| Language | : | English |
| File size | : | 2559 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 177 pages |
| Lending | : | Enabled |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Laure Paillex
Laure Paillex Fidel C Rodriguez
Fidel C Rodriguez Marisol Enchufa
Marisol Enchufa Eve Ensler
Eve Ensler Andrew Faulkner
Andrew Faulkner Larry Semento
Larry Semento Patty Bear
Patty Bear Marita Sydow Hamann
Marita Sydow Hamann Laura Nowlin
Laura Nowlin Whit Hill
Whit Hill Mike Curato
Mike Curato James Carver
James Carver Sally J Rogers
Sally J Rogers Family Traditions Publishing
Family Traditions Publishing Shanlynn Walker
Shanlynn Walker Mick Kilburn
Mick Kilburn Mark Sable
Mark Sable Felicity Pine
Felicity Pine F A Hayek
F A Hayek Holly Winter Huppert
Holly Winter Huppert
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Colt SimmonsNew Moon Rising: Samantha Moon Origins - Delve into the Enigmatic Beginnings...
Colt SimmonsNew Moon Rising: Samantha Moon Origins - Delve into the Enigmatic Beginnings...
 Diego BlairUnveil the Enchanting Adventure: Princess Mirabella and the Zombie Who Came...
Diego BlairUnveil the Enchanting Adventure: Princess Mirabella and the Zombie Who Came... Charles BukowskiFollow ·9.6k
Charles BukowskiFollow ·9.6k Tyler NelsonFollow ·13.9k
Tyler NelsonFollow ·13.9k Truman CapoteFollow ·9.6k
Truman CapoteFollow ·9.6k Yasushi InoueFollow ·15k
Yasushi InoueFollow ·15k Isaias BlairFollow ·15.5k
Isaias BlairFollow ·15.5k Will WardFollow ·8k
Will WardFollow ·8k Frank MitchellFollow ·13k
Frank MitchellFollow ·13k Robert ReedFollow ·18.7k
Robert ReedFollow ·18.7k

 W.H. Auden
W.H. AudenStep into a World of Thrilling Deception: Don Blink by...
Unveiling the Masterpiece of Suspense:...

 Jaylen Mitchell
Jaylen MitchellUnleash Your Creativity with "This Easy Origami": A...
: Embark on an Enchanting Voyage into the...

 Vladimir Nabokov
Vladimir NabokovEmpowering Home Births: A Comprehensive Guide for Fathers...
An In-Depth Exploration of Paternal...

 Juan Rulfo
Juan RulfoThe Maya Exodus: Indigenous Struggle for Citizenship in...
The Maya Exodus: Indigenous Struggle for...

 Julio Ramón Ribeyro
Julio Ramón RibeyroKana Made Easy: Dive into Japanese the Fun and Effortless...
Unveiling the Secrets...
4.3 out of 5
| Language | : | English |
| File size | : | 2559 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Print length | : | 177 pages |
| Lending | : | Enabled |